Leading and Lagging Indicators: In Baseball and in Business
- Google and Yahoo will implement new authentication requirements for emails in February, affecting non-compliant senders with potential delays, blocks, or spam filtering.
- The changes focus on three key aspects: ease of unsubscribing, sending only desired emails, and email authentication.
- Email authentication aims to address email vulnerabilities, prevent fraud and crimes, and provide additional benefits such as avoiding real-message rejections, preventing misuse of your brand, and more.
- Three authentication methods work together to enhance security.
Here are three questions that may interest you and encourage you to read on:
- Is email communication important for your business?
- Do you also use it for lead generation and sales?
- Do you use email delivery service providers?
In February of this year, both Google and Yahoo will have new authentication, consent, and interaction requirements for emails. Senders who do not meet these requirements will experience delays, blocks, or have their emails sent to spam. These changes primarily focus on three areas:
- Ease of unsubscribing. Every sender should be able to unsubscribe from marketing emails with a single click.
- Sending only desired emails. This refers to maintaining spam rates of no more than 0.1% (maximum 0.3%) to avoid delivery issues to recipients.
- Email authentication. Authentication methods must be used on all outgoing emails.
While the first two are easy to control with good mailing software like HubSpot, the last one is more complex. We explain more about it below.
Email Authentication
Email has had a vulnerability since its inception that has facilitated the work of those resorting to fraud, extortion, identity theft, and other crimes using this communication channel.
Therefore, over the years as the tool has become popular, three different methods have been developed to try to prevent others from using your email address for illicit activities.
It is also important to understand that if your company advances in these three methods of protection, email providers' SPAM filters will have more confidence in your domain (e.g., mycompany.com), and you will avoid more of your real emails from your team going to SPAM or even being rejected.
By addressing this serious security issue, other benefits are also generated, such as:
- Preventing the use of your brand and email domain for committing illicit acts against others or even against your own employees.
- Monitoring email traffic worldwide to identify possible illicit activities.
- Complying with current legislation in some countries and/or industries.
- Among others.
The three methods of authentication
Circling back to the three methods we have at our disposal to increase our email authentication capacity and prevent misuse of our email addresses, here is a brief description of each one:
- Method 1. SPF (Sender Policy Framework) was invented in 2003 and aims to allow you as the owner of your email addresses to publish an official list of servers (IP addresses) authorized to send emails on your behalf.
- Method 2. DKIM (DomainKeys Identified Mail) was invented in 2005 and is a "digital seal" added to each email sent so that if someone alters the email between when you send it and the recipient receives it, the seal is "broken" and cannot be authenticated.
- Method 3. DMARC (Domain-based Message Authentication, Reporting & Conformance) is a standard that relies on SPF and DKIM to validate alignment between the sending server's domains (validated by SPF) or the digital seal server's domains (validated by DKIM) and the email in the From address that you receive in an email.
The vulnerability we mentioned earlier about how email works leaves a gap even if you use the first two methods; there is still a problem that is only resolved by also implementing the third method through what is known as "alignment." Below, we explain why.
Alignment
There are three relevant pieces of information used for authentication within an email:
- The sending server's domain (called Return-Path), is the actual server from which an email is sent and is validated with SPF.
- The authorized domain is within the DKIM security seal, which is validated with the key used by DKIM.
- The domain claimed to be sending the email (called From Address) and which is what we see in the Form address.
Este tercer campo de información es muy relevante porqué es la única dirección de envío que está normalmente visible a los usuarios. Tanto el dominio del servidor de envío, cómo el dominio autorizado por DKIM son campos que van ocultos dentro de un correo electrónico. Consulta cualquier correo electronico recibido y te darás cuenta que la única información visible sobre quién envía dicho correo es el "De:", por ejemplo:
The third piece of information is very relevant because it is the only email address visible to users. Both the sending server's domain and the domain authorized by DKIM are hidden fields within an email. Take a look at any received email in your inbox and you will see the only visible information about who sent the email is the "From:" address, for example:
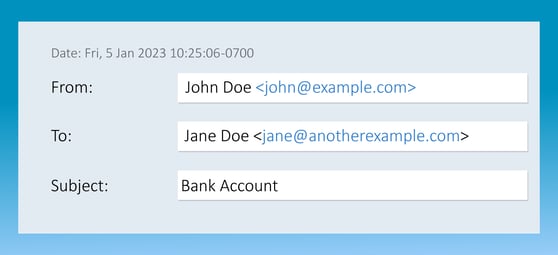
However, the vulnerability previously mentioned allows this last information to be easily altered by someone seeking to scam. And given is the only visible information to you as a user, it makes it easier to commit an illicit act.
In other words, a more sophisticated wrongdoer could potentially pass SPF and DKIM but still have falsified the "From address" of an email and thus deceive potential victims using your email address.
This is where the third authentication method we have developed for email authentication comes in, DMARC, as previously described is a standard that relies on SPF and/or DKIM; and validates alignment between the hidden validated domains and the email in the "From address" that you receive in an email.
What is DMARC?
Let's look at an example. A potential extortionist could send an email to one of your collaborators pretending to be a director and requesting sensitive information or payment. Being a sophisticated extortionist, they would take care to pass SPF from a fake server and use the "From" (From address) to deceive, something like:
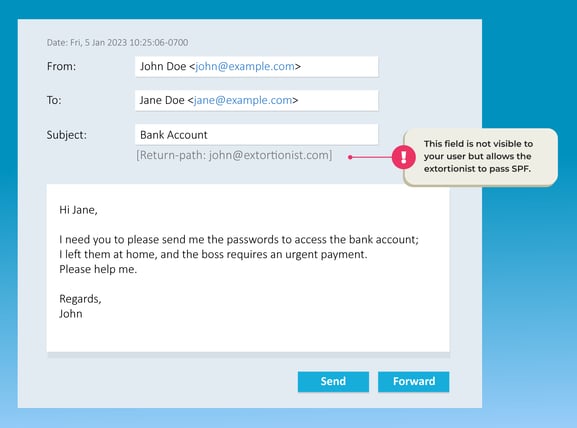
DMARC relies on SPF and DKIM and aims to precisely align an email that could be authenticated with either of these methods (SPF and/or DKIM) with the From address in the email. In this hypothetical case, the email would have passed SPF/DKIM but not DMARC, allowing the detection that it is an illicit email.

Now, DMARC not only goes up to identification; it actually contains functionality for controlling policies on what to do with emails that fail authentication, ranging from relaxed to strict policies. These policies can require email providers to take no action, quarantine, or even reject such illicit emails.
All of this generates more security with obvious advantages in preventing illicit acts, but also with the additional benefits mentioned earlier, which are generated when your email is more reliable due to appropriate policies for detecting and controlling illicit acts.
Contact Us
¿Need more assistance?
If you need more information on these requirements or assistance with email authentication in your organization, feel free to contact us for personalized solutions.


.jpg?width=500&height=500&name=myriam-jessier-eveI7MOcSmw-unsplash%20(1).jpg)